
Modern android smartphones security have the technology to protect the files we store from malware or theft. There are some steps we all need to take in order to protect our files and our mobile. The steps mentioned above can be done on all devices running an android operating system.
Android Security code on mobile smartphone
On all smartphones, the user should enter a security code and fingerprint if available in the functions of the device. Avoid patterns because they are easy to spot by a malicious user. Prefer hard 6-digit pin or whole key phrase.
Unknown sources disabled

From the beginning by security, all android smartphones have unknown sources in the settings menu turned off. But when a website goes to install a .apk application on your smartphone, it activates the menu in unknown sources to activate it.
Access applications that you are sure are not malicious and go to Settings in Unknown Sources to see if they are disabled after installation or the application has left the option permanently enabled.
Usb debugging disabled
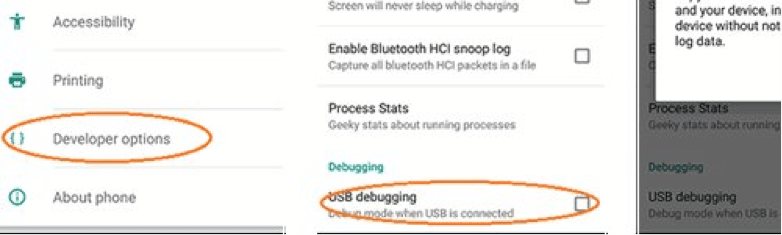
This option is in the hidden menu of developers. Great attention to this option once someone activates it. From the beginning, usb debugging is disabled. However, there are applications that may require you to enable usb debugging. This option can open up incredible holes in the security of the android mobile phone to a malicious user or hacker.
Encrypted user data
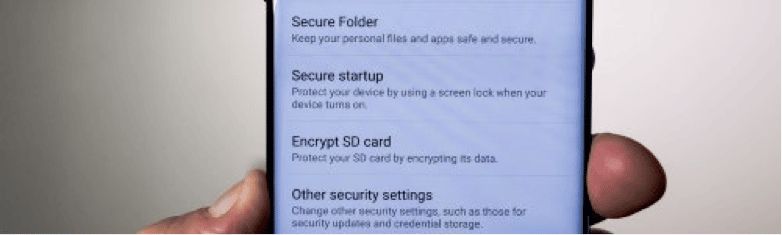
All android smartphones have an option in the settings / security menu that allows the user to encrypt the files he saves. This option makes the phone start up a little slower (in seconds), but it offers incredible security in our data and the guarantee that nobody will gain access to our files in case of theft.
Locked bootloader
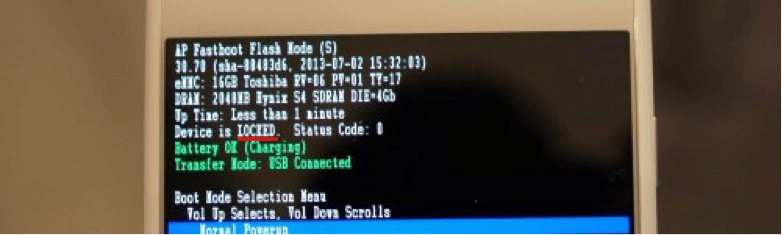
Right from the start all android smartphones have a locked bootloader except some xiaomi imported from China and the vendors unlock them to get global rom.
Anyone experimenting and unlocking the bootloader to pass a custom rom doesn’t just open the back door to their data but the whole portal with lighting and red carpet. The locked bootloader along with usb debugging disabled are the two most important steps for software security.
Android Smartphone Security – Manufacturer account
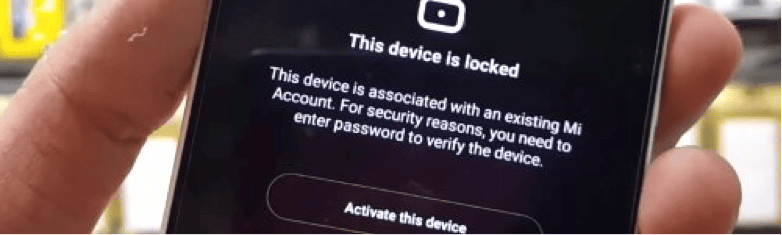
Most people neglect to create accounts on the manufacturer’s servers and are simply content in a gmail. Samsung account, Huawei ID, Mi account, LG account etc are essential to secure even more data and access to our smartphone.
The account on the manufacturer’s server can guarantee not only security but also the location of the device.
Free VPN internet

Many users use applications that give them free internet access without data from the provider. These applications create a communication channel between the device, the application server and the internet.
However, this results in the server controlling the traffic, data and passwords you use on various sites. The reliability of these applications is questionable and their use is dangerous as we expose our data to a stranger. It is good to avoid them.
Free Wifi Spots

In the free wifi spots, malicious users can easily gain access to your device through your shared router. If wifi is connected and a computer running linux then things can be even more dangerous. There are applications on linux that can access smartphones passwords through social media etc through the router.
Encryption applications
Use applications that can encrypt your written or oral conversations such as viber. This way even having access to our monitored device can not interfere with the conversation. The same is true if you access the device via wifi.
1 thought on “Android Smartphones and Security”